Description
Can you find a way out of this loop?
Solution
If we extract the Eternal Loop.zip file we found the 37366.zip file. This file is password protected and contains the 5900.zip file. We don’t know the 37366.zip password… We’ll try with 5900… It works! Now we know that the zip file will be the name of the inner file.
Ok, the challenge now is unzip the files until we get the last file. We can do this by hand, but, spoiler alert: There will be 501 zips! To do this I did a self-explained python script that you can see here: eternal_loop.py
Once we have the last file, surprise, is password protected. This time we have not clue what the password might be, so we’ll bruteforce it.
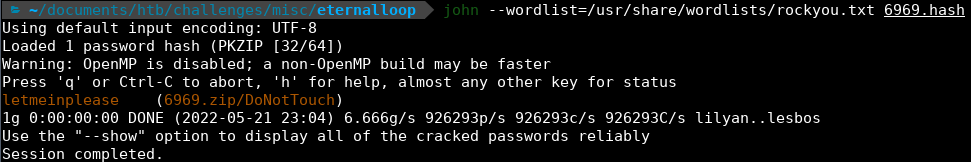
First of all is extract the hash of the zip file. We’ll use zip2john
1
zip2john 6969.zip > 6969.hash
Once we have the hash we’ll bruteforce it with john using the rockyou.txt file
1
john --wordlist=/usr/share/wordlist/rockyou.txt 6969.hash
We get the password, so we can extract the 6969.zip file.
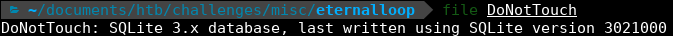
Once extracted we have a DoNotTouch file. The file is binary and, if we apply the file command to see what type of file it is, we can see that is a SQlite 3.x database.
So, we have to open the database
1
sqlite3 DoNotTouch
Once the database is open we can list the tables with the command .tables
1
.tables
And we can export the tables data to csv files following the next steps:
- Configure to display headers
- Set the output mode
1
2
.headers on
.mode csv
- And export the data for each table:
1
2
.output data.csv
select * from table;
Now we can grep the csv files looking for the flag. To speed this step up I will tell you that the flag is in the employees table, in the email field for the employee wiht id 69.
1
select Email from employees where EmployeeId = 69;
Enjoy! ;)